Introducing Cloud Identity Insights for Sysdig Secure
In recent years, almost every major cloud breach has been marked by overly permissive credentials, followed by lateral movement and privilege escalation. These vulnerabilities have allowed attackers to navigate through systems with ease, escalating their privileges to cause significant harm. It’s crucial for cloud threat responders to be aware of threats as they occur and to be able to contain these attacks swiftly and effectively.
Identity plays a critical role as the connective tissue in investigations, providing the necessary context to understand and trace the actions of users. Sysdig stands at the forefront of this need by offering solutions to manage your identity security. With Sysdig, organizations can prevent attacks by strengthening their identity posture, and detect anomalous or suspicious actions executed by users, ensuring a robust defense against potential threats. This proactive approach not only fortifies security, but also enhances the ability to respond to incidents in real time, making it an indispensable tool in modern cybersecurity.
What’s new: Cloud Identity Insights
Cloud Identity Insights provides the context organizations need to get ahead of attacks and take action before threat actors abuse compromised user accounts. This new addition enhances Sysdig’s cloud detection and response (CDR) capabilities, making it simple to correlate identity behavior with events and detect and respond to potentially compromised users. It also helps teams prevent similar attacks in the future. Armed with these new capabilities, security teams can respond immediately to contain attacks in motion and strengthen identity posture to enforce zero trust in the cloud.
Potentially compromised users
Misconfigured identities and secrets often serve as the initial access points for attackers, making them critical vulnerabilities in any security strategy. Sysdig addresses this issue by detecting abnormal activity, including patterns of actions commonly observed during various phases of a breach. This proactive detection is vital for incident responders, who need to be notified when a user is potentially compromised so they can promptly start investigating the incident. By identifying and addressing these early indicators of compromise, Sysdig helps to fortify security defenses and enable quicker, more effective responses to potential threats.
Compromised users
Incident responders need the ability to quickly confirm whether or not a user is genuinely compromised so they can appropriately escalate or deescalate the situation. The capability to flag a user as confirmed compromised creates a clear signal to the team that the incident has been thoroughly triaged and is not a false positive. This ensures a focused and efficient response, allowing the team to prioritize and address actual threats without being sidetracked by false alarms.
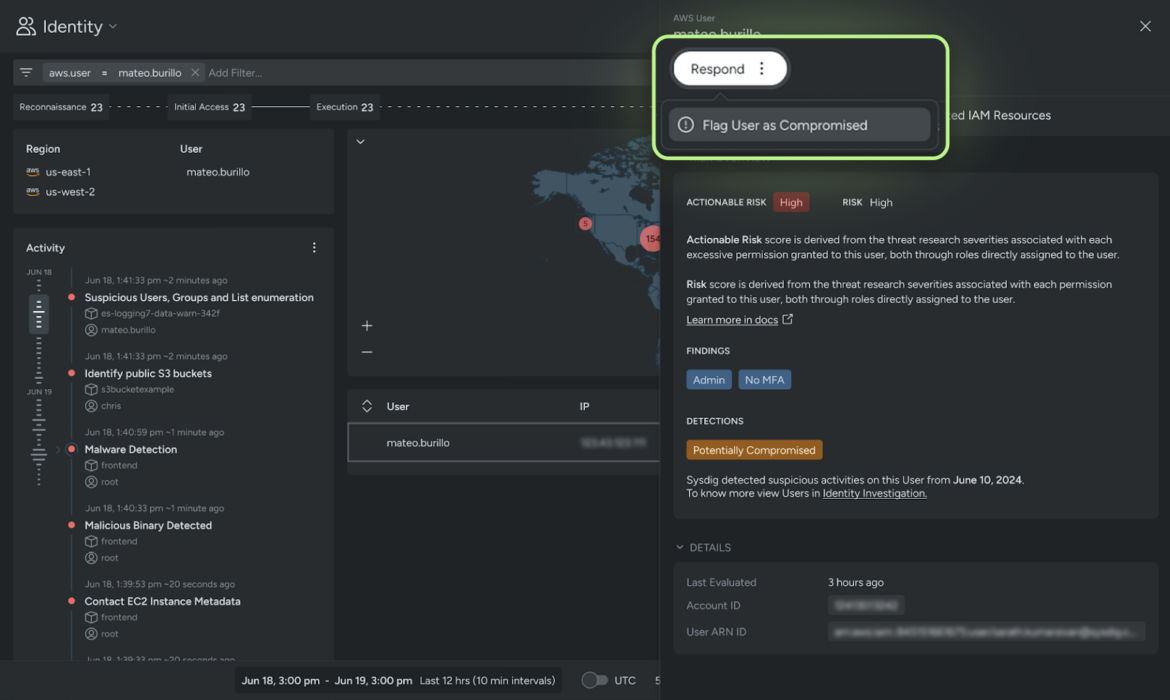
Contain compromise
Cloud threat responders must be equipped with the knowledge and tools to halt an attack that is actively in progress so they can contain the threat and protect their business. When a user is flagged as potentially compromised, Sysdig steps in to offer a range of options, each with varying levels of intensity, to contain the compromise effectively. Potential actions can range from deleting and creating new access keys all the way to deactivating or deleting a user.
Sysdig provides detailed playbooks for each option, guiding responders through the steps necessary to contain the compromise. This structured approach allows responders to act swiftly and decisively, minimizing the impact of the attack and safeguarding their organization’s assets.
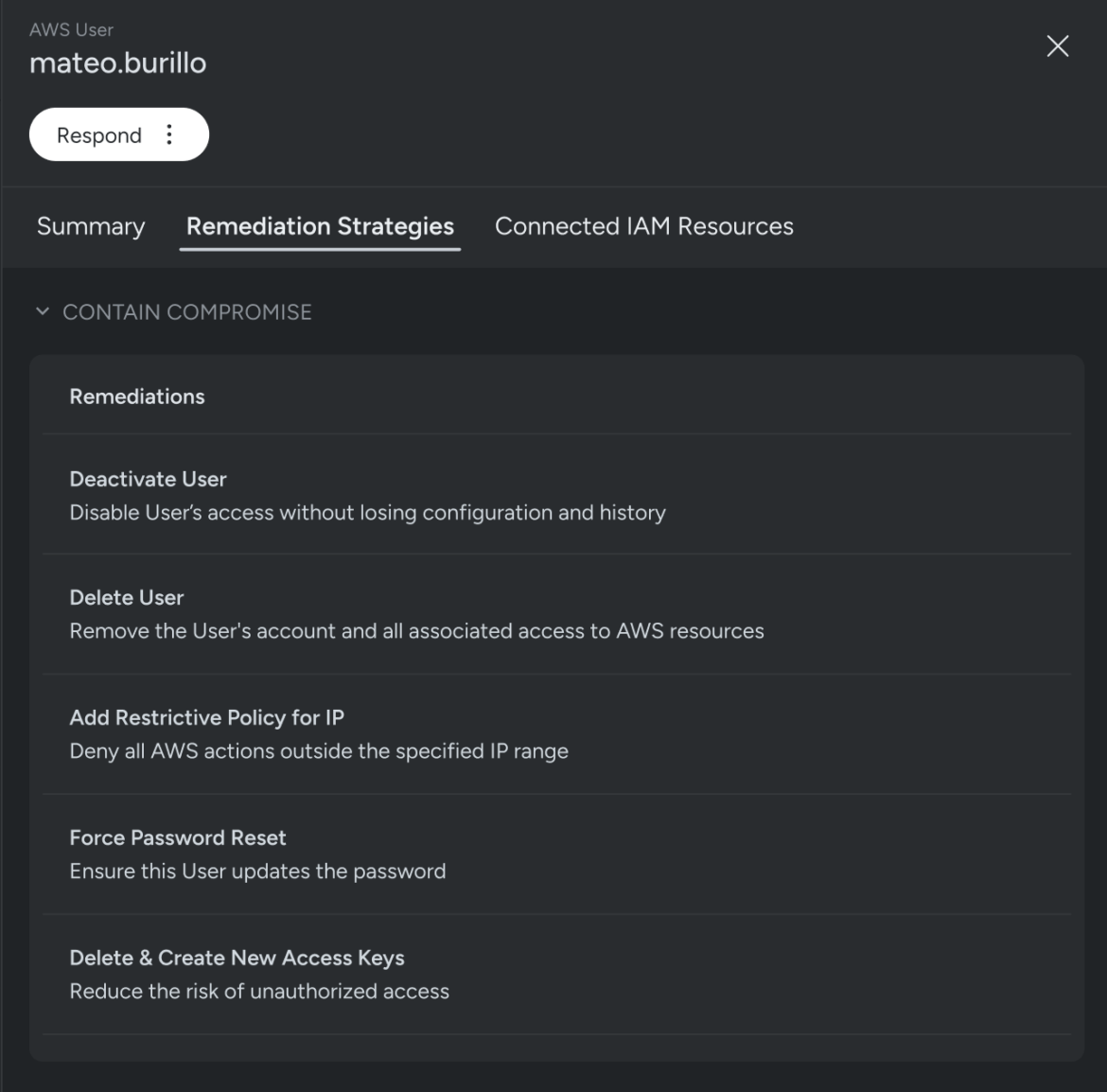
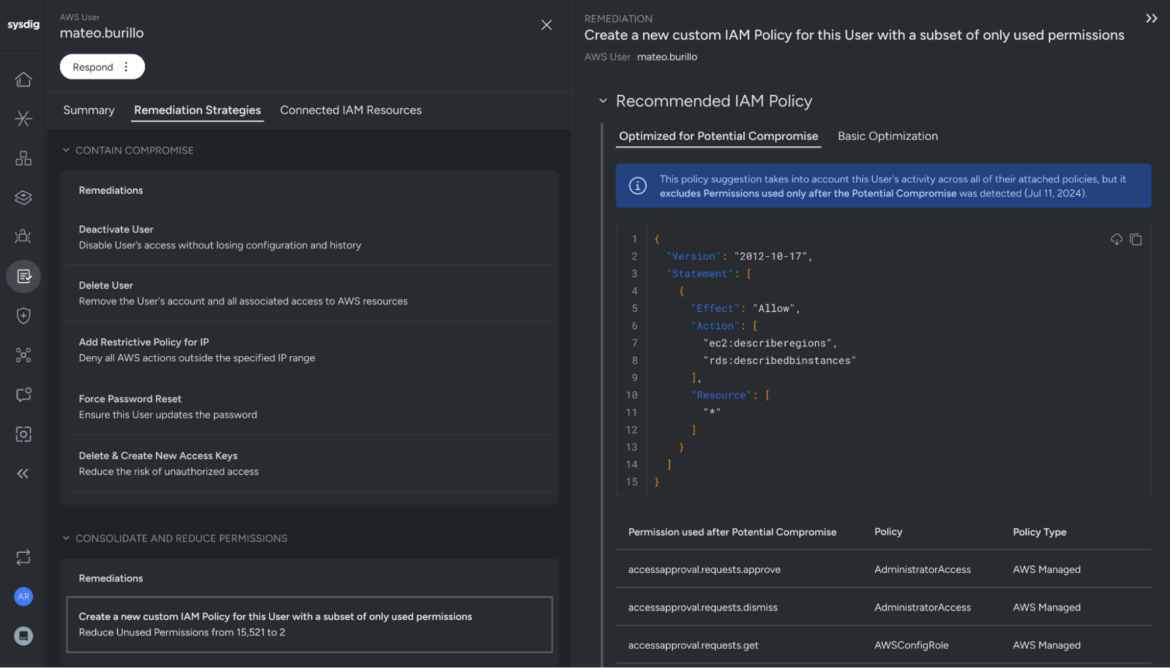
Achieve zero trust through least permissive policy optimization
Achieving zero trust in the cloud fundamentally relies on reaching a state of least permissive access. The Sysdig Threat Research team has discovered that, on average, only two percent of all granted permissions are actually used. To address this, Sysdig generates Least Permissive Policy Optimization suggestions by analyzing cloud logs and including only the permissions that are actively used.
To ensure that these optimizations are not compromised by malicious actions, Sysdig takes a proactive approach. It tracks all permissions used only after a user is flagged as potentially compromised and, by default, excludes these permissions from policy optimizations. This careful scrutiny helps maintain the integrity of security policies, ensuring that only legitimate permissions are granted and reducing the risk of privilege escalation and lateral movement by threat actors.
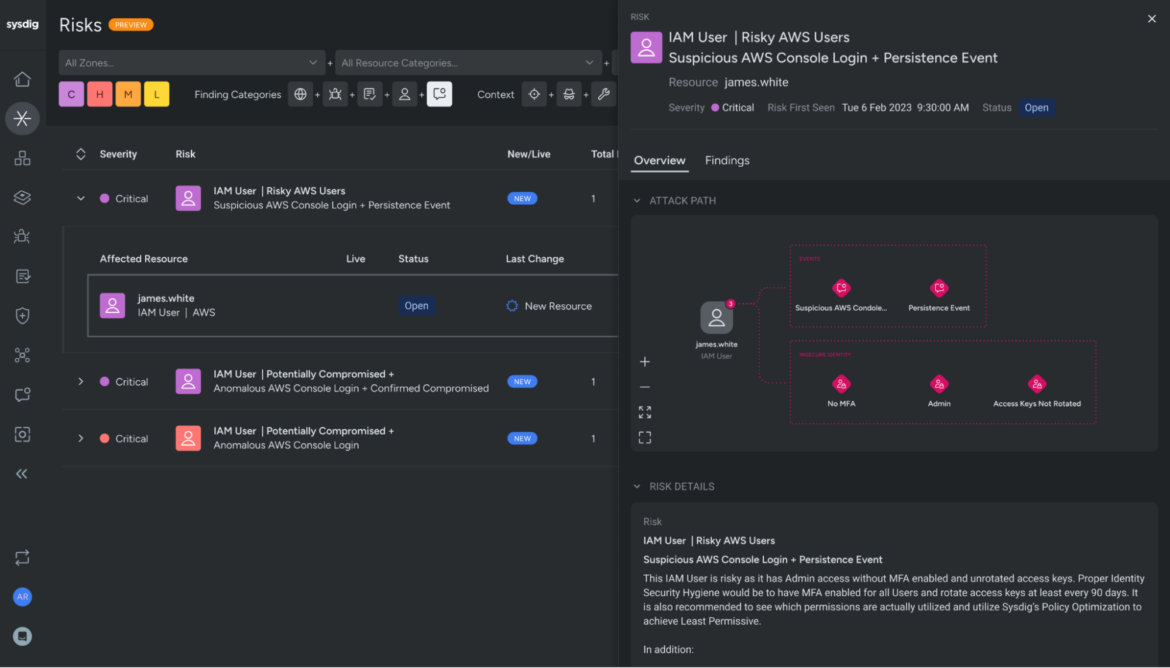
Target your riskiest identities for posture hardening
Since attackers often target identities to gain initial access to environments, security teams should focus on hardening their posture around these entry points. Sysdig assists in this effort by offering opinionated recommendations on which users and roles to target first. On the Risks page, Sysdig highlights the identities that present the highest risk, enabling security teams to prioritize their efforts and strengthen their defenses effectively.
Stop attacks at the first sign of compromise with Cloud Identity Insights
The speed of cloud attacks warrants having real-time threat detection. Identity is a key piece of understanding breaches in order to correlate malicious activity. Flagging users as potentially compromised lets your security response teams know they need to investigate. Sysdig’s Cloud Identity Insights takes into account real-time detection of malicious user activity, and how to harden identity security posture to prevent breaches in the first place.
Join our upcoming deminar, Cloud Identity Insights: Stop Compromised Identities in Minutes, for an interactive showcase of these features.