Shift left with the Sysdig extension for Visual Studio Code
Adversaries exploit security blind spots and sneak through traditional defenses to craft attacks that impact your operations, or even worse, your reputation. One recent example is the Revival Hijack supply-chain attack, where threat actors registered new PyPi projects with names of previously deleted packages.
One way to counter this imminent threat is to “shift left,” or take ownership of the code’s security posture earlier in the development process. To support this cause, Sysdig is introducing an extension for Visual Studio Code (VSCode), now available on the Visual Studio Marketplace.
In this article, we’ll install the extension and learn how it scans Dockerfiles, Docker-compose, and Kubernetes manifests. The extension enables you to do the following:
- Uncover vulnerabilities within software packages
- Scan infrastructure as code (IaC) projects
- Evaluate compliance with Sysdig’s vulnerability management (VM) policies
Empowering developers with Sysdig
The Sysdig extension offers developers preventive measures by integrating security best practices to deliver pre-runtime security. It improves metrics like mean time to repair (MTTR) by reducing the feedback loop between code creation and security review. It also addresses vulnerabilities and compliance gaps before the code reaches production.
Initial configuration
Here are the initial steps to configure this new extension:
- Download the Sysdig Scanner extension from the VSCode Marketplace
- Once installed, launch the Command Palette (
⌘ +Shift+Pon Mac andCtrl+Shift+Pon Linux) - To configure the extension select “Authenticate with Sysdig Secure API Token” and provide your Sysdig Secure URL and API token
This links the extension to your Sysdig account and allows it to retrieve your organization’s security policies.
Further modifications include options to do the following:
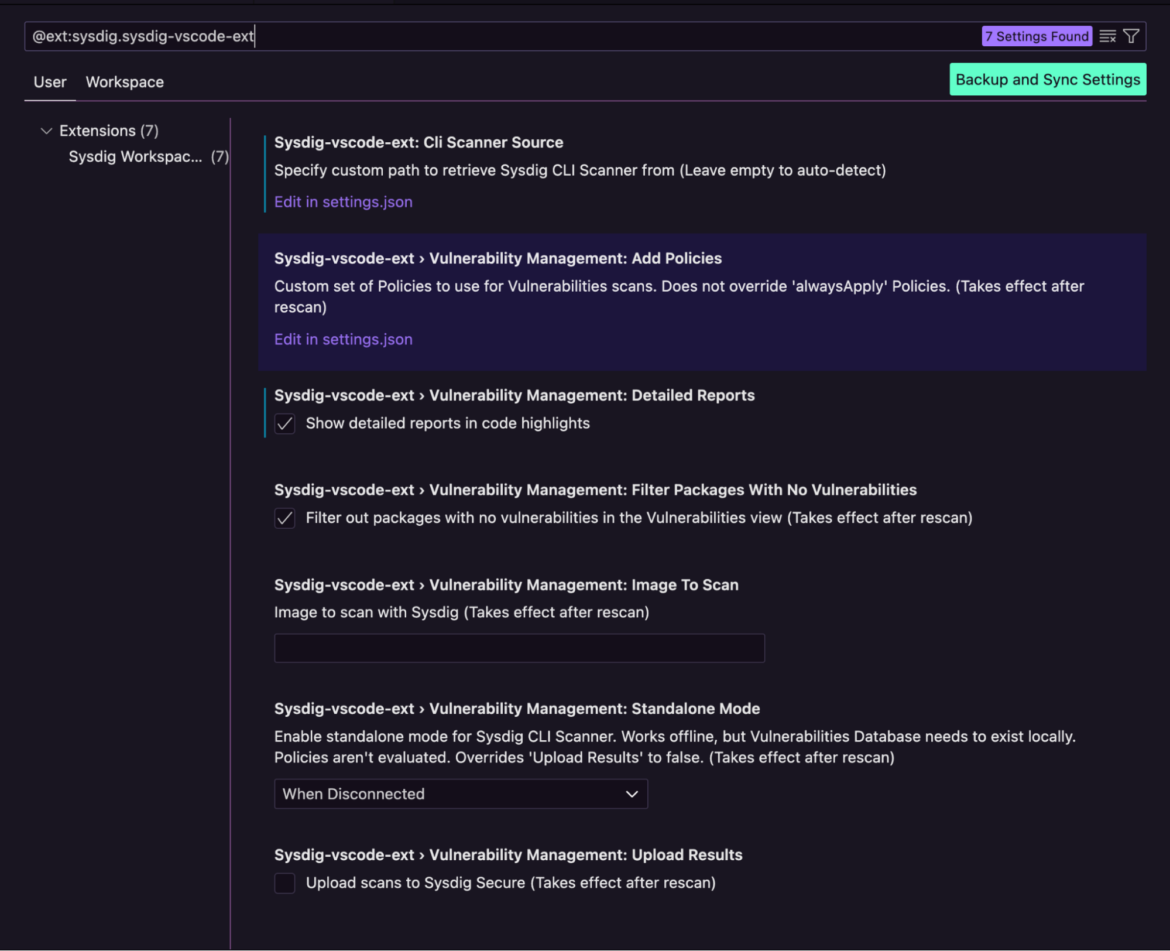
- Define the cli scanner source
- Customize security policies (predefined or custom-built) for vulnerability scans and compliance checks
- Define remote or local images, repositories, and environments to scan
- And many more customization options
Visualize in-depth context with Layered Analysis
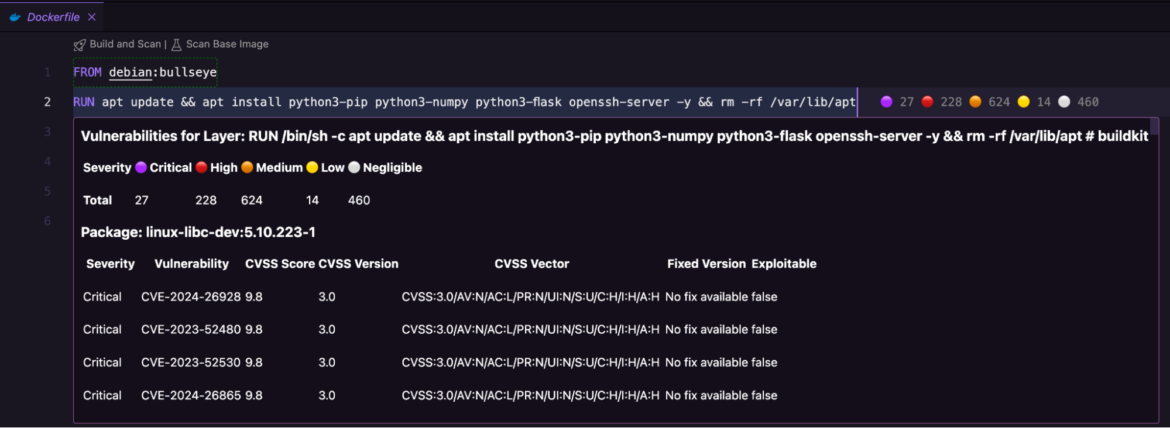
One of the standout features of the new extension is the Layered Analysis in Dockerfiles. It dismantles each layer of an image file to pinpoint the exact line or code instruction that may pose a security risk. This granular insight helps response teams to address security gaps with clinical accuracy, and reduces the overall time it takes to repair an application.
Let’s see this feature in action:
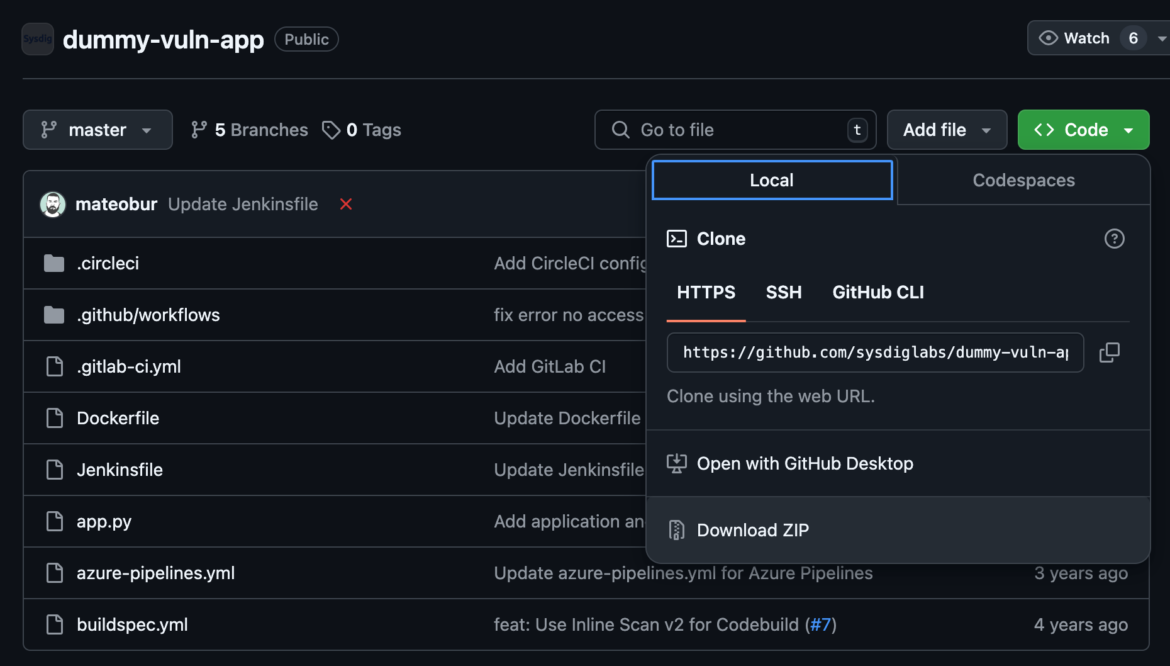
From our Github repository, download the zip file and unzip it in your workspace folder.
Code reviews and security workflows between diverse stakeholders may be seen as an unnecessary ordeal that delays production timelines. To innovate faster, your developers may often bypass security guardrails and introduce unwanted risks.
The Sysdig extension sanitizes software packages before the code is pushed to production, saving critical time and preventing security from slowing down developer workflows.
Next, use Visual Studio Code to open the folder in your workspace.
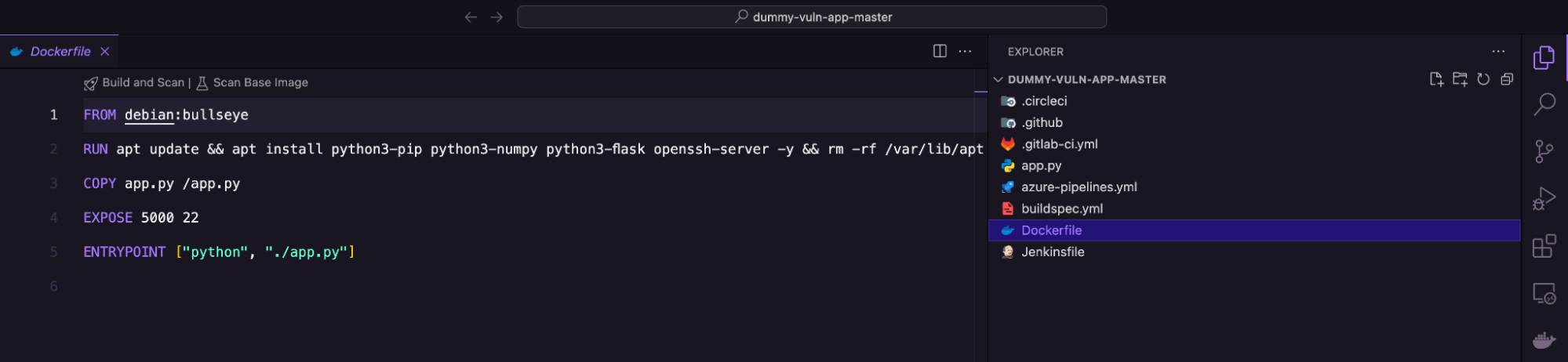
The folder contains a Dockerfile that installs the software binaries required to build a container. We’ll use the Sysdig extension to scan this image file for vulnerabilities. Use the Explorer menu to select the Dockerfile. You’ll notice two options: Build and Scan and Scan Base Image on the top.
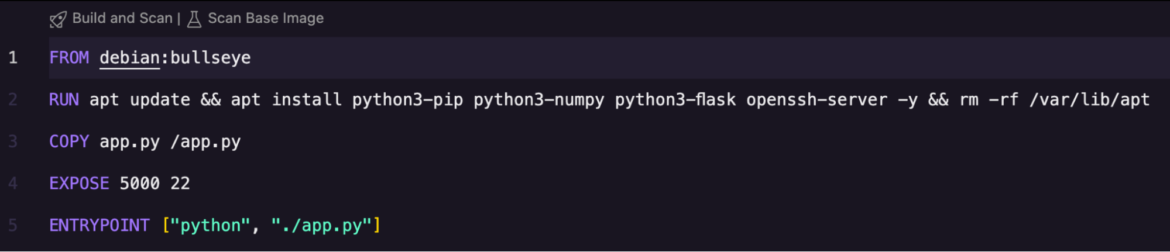
The Sysdig extension offers flexibility, allowing you to build the entire Dockerfile and scan for vulnerabilities in the software packages used, or simply look for security gaps within the base image debian:bullseye.
Either way, your team gets a detailed report of all the detected vulnerabilities. These are categorized by severity (and color), so it’s easier to review and remediate in a timely manner.
Click the Build and Scan option.
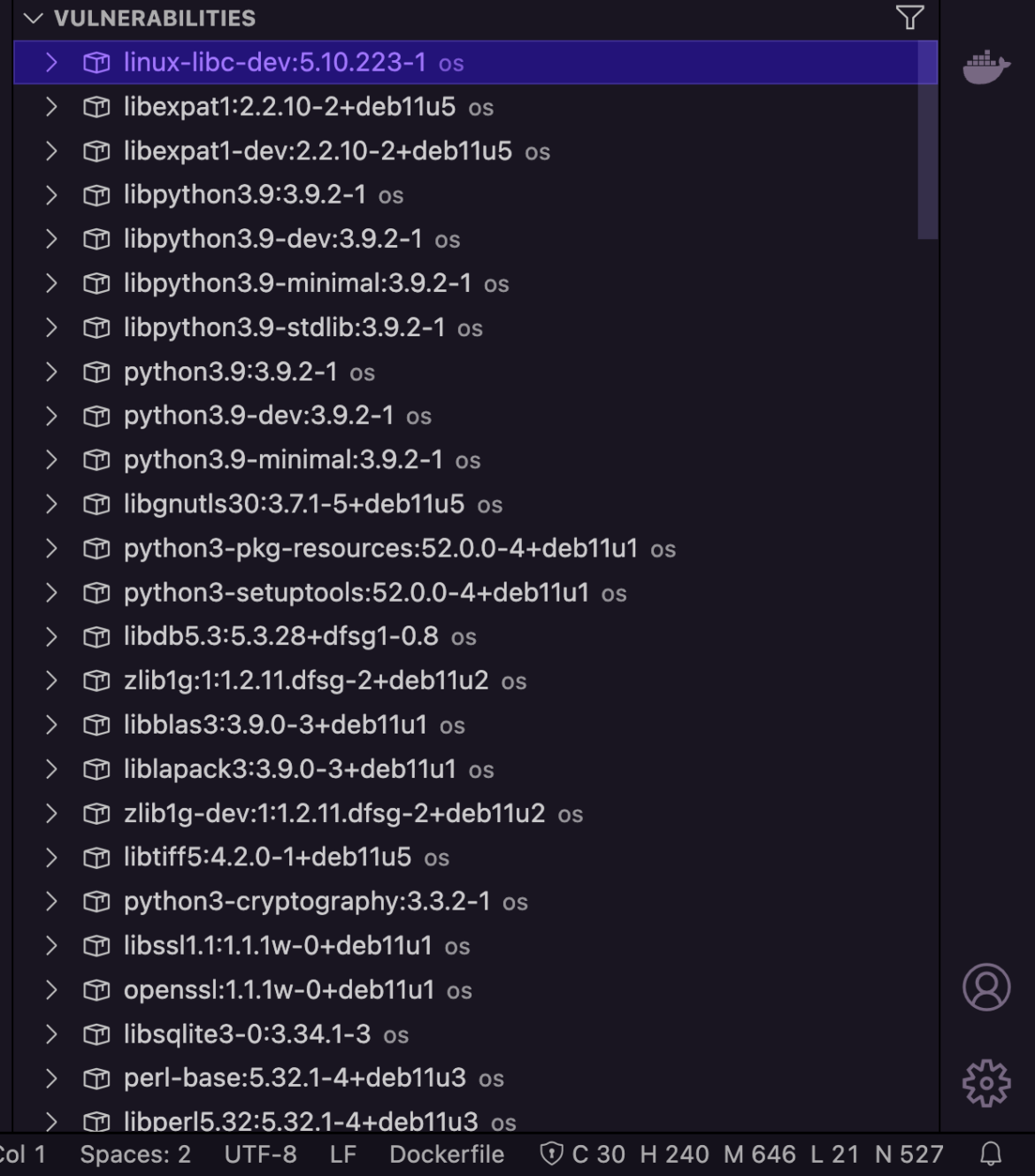
Your team may filter results (Exploitable and Fixable), make informed decisions, and deploy established strategies to either contain or reduce the adversary’s ability to compromise your environment and escape.
While the Sysdig extension offers powerful scanning capabilities, there are some limitations to be aware of:
- Non-concurrent scanning — Scans are performed sequentially, which might affect performance in large projects
- Multiple YAML support — The extension currently does not support scanning multiple Kubernetes or Docker-compose YAML files in a single run
- ARG statements in Dockerfiles — Scanning does not currently resolve ARG statements (build arguments), which may limit the detection of vulnerabilities in certain scenarios
Secure your Infrastructure as code projects
We saw how the new Sysdig extension for Visual Studio assists in developer oversight and prevents any vulnerabilities from creeping into your development code.
This use case can be extended to include scanning of IaC projects too. Whether the software files are Terraform, CloudFormation, or other IaC tools, the extension secures the entire codebase, and aligns it to governance frameworks and compliance policies that are tailored to your defined posture.
As in the previous example, we’ll use the Sysdig extension to scan Terraform files and Kubernetes manifests.
Download the file from Github, unzip it in your workspace, and open the folder using Visual Studio.
Launch the Command Palette to Scan Workspace for IaC Files with Sysdig.
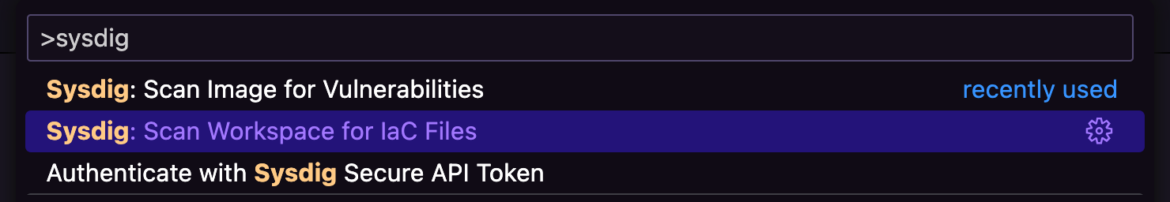
Sysdig scans the entire workspace, including the Terraform and Kubernetes manifests, to list all misconfigurations associated with these files. This provides the necessary context needed by security teams to engage diverse skill sets and deploy timely responses.
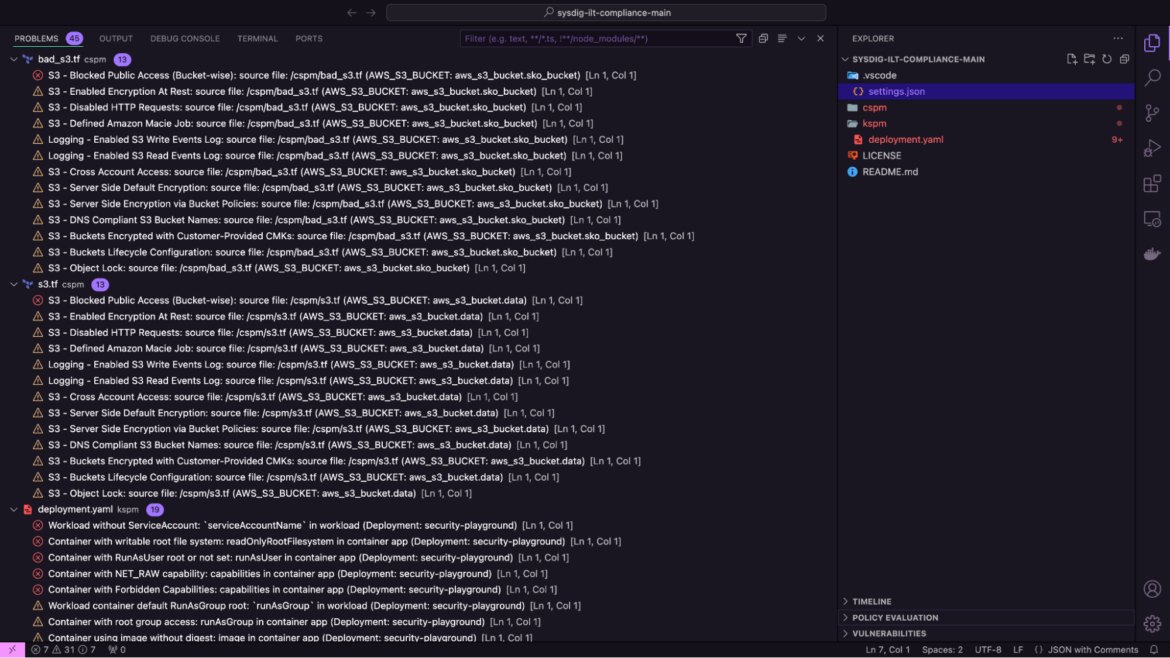
Ensure compliance
We know developers are under tremendous pressure to deliver their code on time. Their productivity is typically measured by internal metrics, like lead time, cycle time, change failure rate, deployment frequency, mean time between failures (MTBF), and mean time to recover/repair (MTTR).
Besides addressing security risks, developers are also expected to ensure their work complies with government and organizational policy frameworks. If compliance is neglected, it may lead to heavy fines and cause a reputation loss in the market.
The new Sysdig extension lends a helping hand to developers by identifying all compliance violations prior to code deployment.
In this example, we’ll create a custom policy (ACME) using Sysdig Secure, define it within the extension settings in Visual Studio, and scan the vulnerable Dockerfile image previously downloaded.
- In Sysdig Secure, create a new pipeline policy ACME Policy.
- Enable predefined rule bundles that align with the NIST framework.
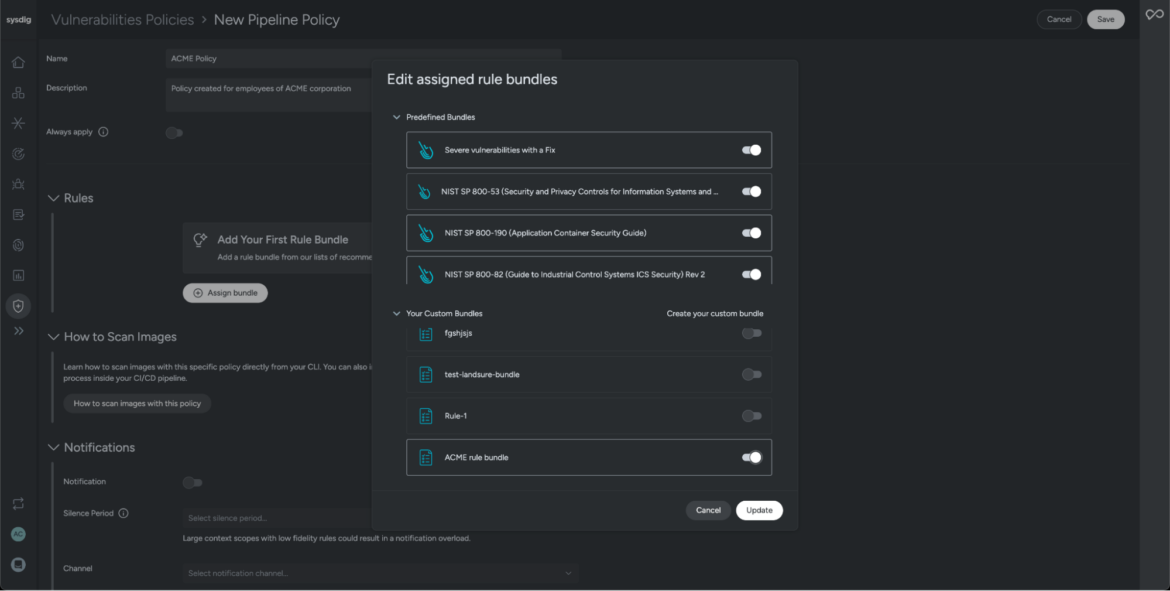
Rules in Sysdig are curated and maintained by the Threat Research Team. They are generally associated with runtime or pipeline policies based on the enterprises’ need to improve their security posture.
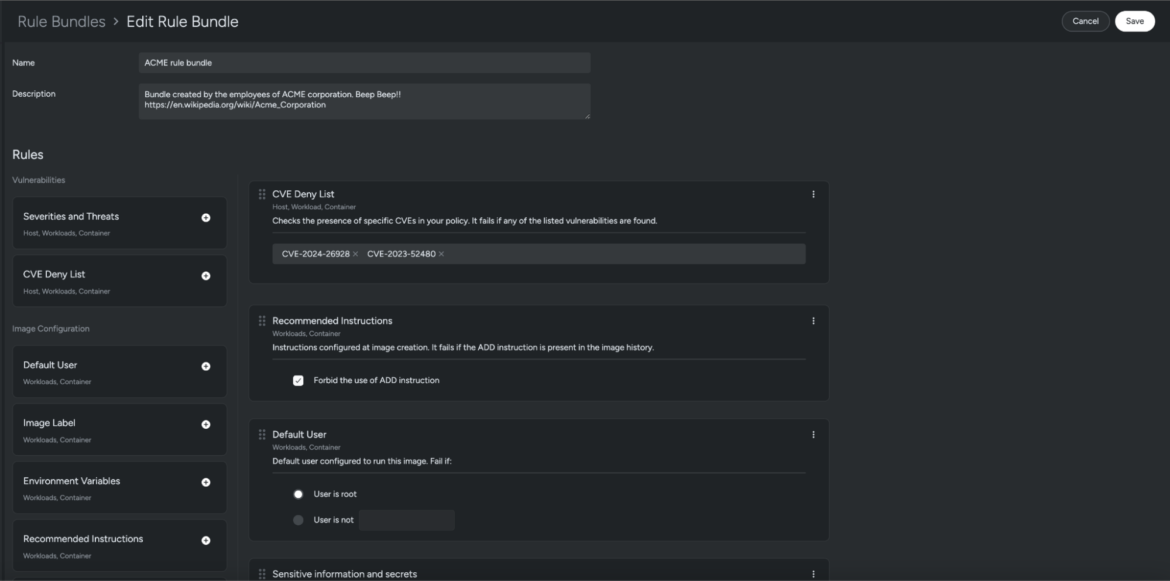
The platform also gives you the flexibility to define custom rules and assign them to your policies. These rules trigger when critical vulnerabilities are detected.
The below image is an example of how you’d create a custom rule bundle in Sysdig Secure.
Now we need to link this custom policy with the Sysdig extension running in our Visual Studio.
Add the policy names under Sysdig extension settings.

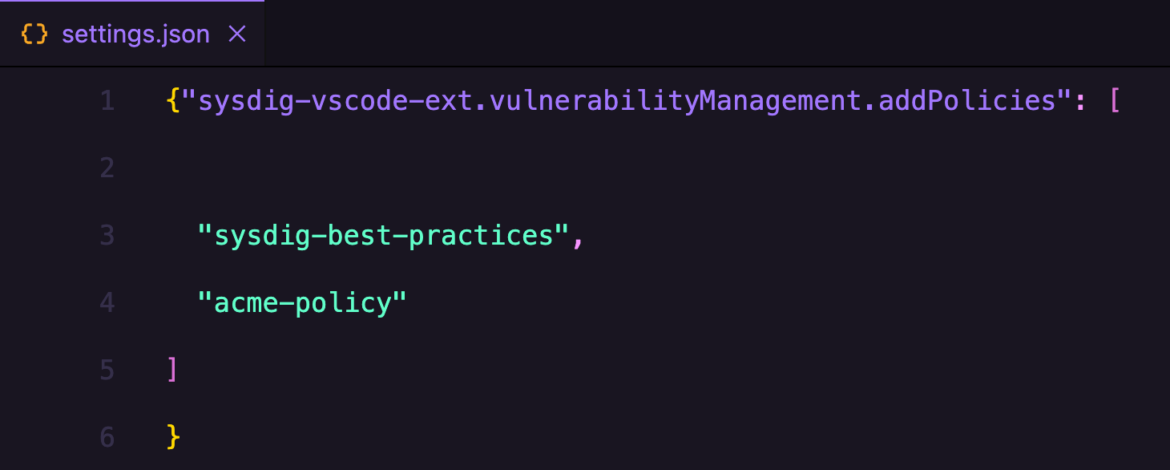
Alternatively, you can navigate to extension settings and add these policies in the .json file.
.Launch the Command Palette and select Scan Image for Vulnerabilities.

Add the folder name sysdiglabs/dummy-vuln-app (previously downloaded) and hit Enter.
The Sysdig extension scans our folder and reports vulnerabilities along with the policy violations it detected during the scan. Based on your risk appetite, your team can make quick informed decisions and reduce your losses.

By integrating these Sysdig scans into your workflow, you can catch and fix vulnerabilities in the software packages that are used in a project early, ensuring the project’s security and compliance before it ever leaves your machine.
Take ownership of your code’s security posture
The Sysdig extension empowers developers to take full ownership of the security context of their code. It optimizes their workflows to adopt secure coding practices and define goals that secure the software’s data and functionality from unauthorized access, modification, or disruption. This not only improves the security posture of containerized application stacks, but also fosters a more proactive approach to security within development teams.
If you like using the extension, don’t forget to leave a review in the Marketplace!