Introducing New Investigation Features for Sysdig Secure
Cloud migration and continuous innovation provide organizations with substantial gains in speed, scalability, and cost (to name a few). Most security teams have no choice but to make the jump to the cloud, in at least some capacity, to support and protect this rapidly expanding attack surface.
But organizations and security teams aren’t alone. Threat actors have been readily adapting their craft to take advantage of cloud speed. As a result, cloud attacks happen fast, rapidly weaving through a target’s cloud estate and drawing on extensive capabilities to achieve their goals.
A prime example is the SCARLETEEL attack, which can infiltrate an organization, execute cryptominers, uncover cloud credentials, pivot to other cloud accounts, and ultimately exfiltrate proprietary data – all in just 220 seconds. Investigating cloud attacks like SCARLETEEL has traditionally been a laborious, error-prone, and manual process. The odds are stacked against defenders, and the reality is that security teams are often unable to investigate threats before the attack completes.
That’s why the 5/5/5 Benchmark for Cloud Detection and Response – the only industry standard for cloud security – establishes that you have just five minutes to perform cloud investigations to head off attacks before they can be executed.
What’s new: Enhanced investigations capabilities
Today, Sysdig is streamlining cloud detection and response (CDR) use cases by automating the collection and correlation of events, posture, and vulnerabilities to identities. The cloud context these capabilities provide is unparalleled. An interactive visualization of this information helps analysts instantly conceptualize attacks, unlocking five-minute investigations across the most advanced threats.
The key new capabilities enhancing investigations include:
Attack chain visualization
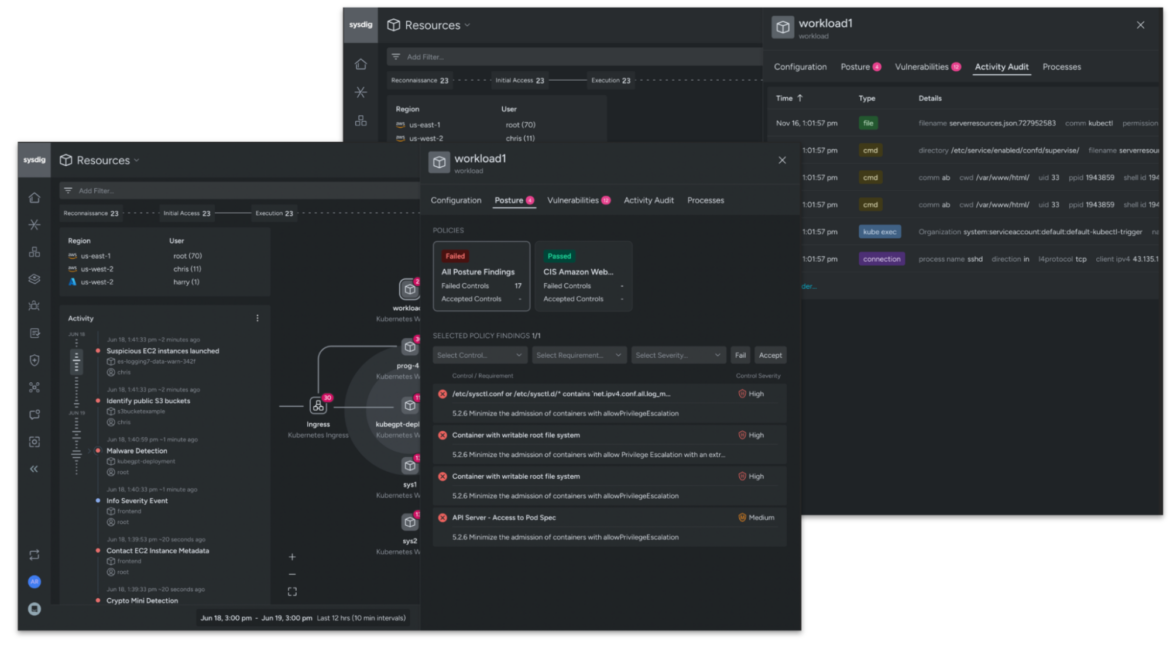
Security teams can leverage any alert or suspicious finding as a starting point to launch an investigation with the Sysdig Cloud Attack Graph. The graph provides attack chain visualization and empowers security analysts to rapidly understand the relationships between resources, and their implications for the attack chain across any cloud environment.
Sysdig’s attack chain visualization accelerates investigations by automatically correlating cloud and workload events to identities. Deep context from command history, as well as network and file activity, is easily gleaned from the overlays. Sysdig’s automated captures enable analysts to dig deeper by automatically tying digital forensic evidence to the events. Real-time context is combined with vulnerabilities and misconfiguration findings to provide a comprehensive and holistic view of a threat. To further simplify workflows, and narrow an investigation window when necessary, all investigations are MITRE-mapped and filterable.
Real-time identity correlation
At their core, all cloud attacks revolve around identities. Whether it be human or machine, one or many, analysts need a way to stitch suspicious findings to identities and their associated behaviors. Sysdig’s enhanced investigation capabilities automatically correlate cloud events with enriched identity data. Using attack chain visualization, analysts can rapidly understand suspicious identity behaviors such as unusual logins, impossible travel scenarios, and malicious IP addresses. With this context, teams can rapidly understand the who, what, where, and how of threat actors in their infrastructure.
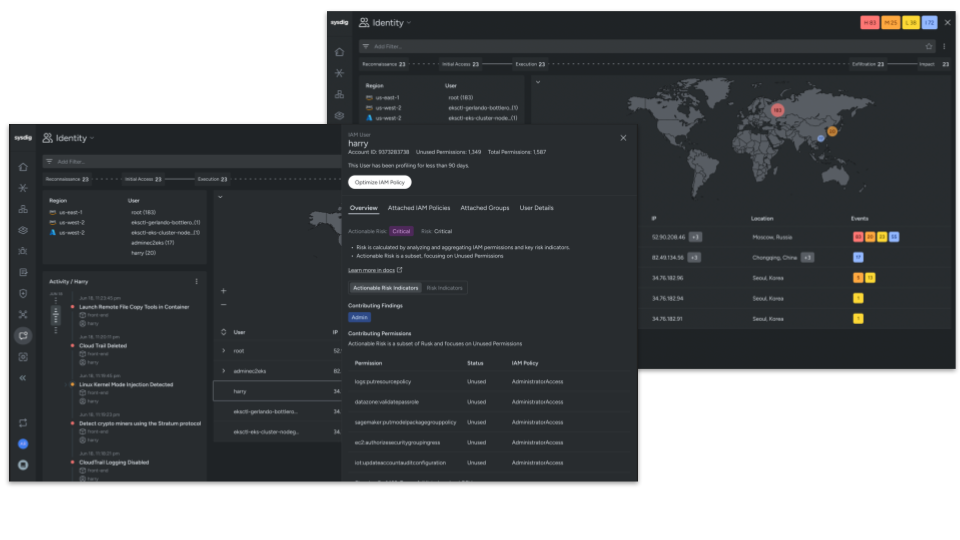
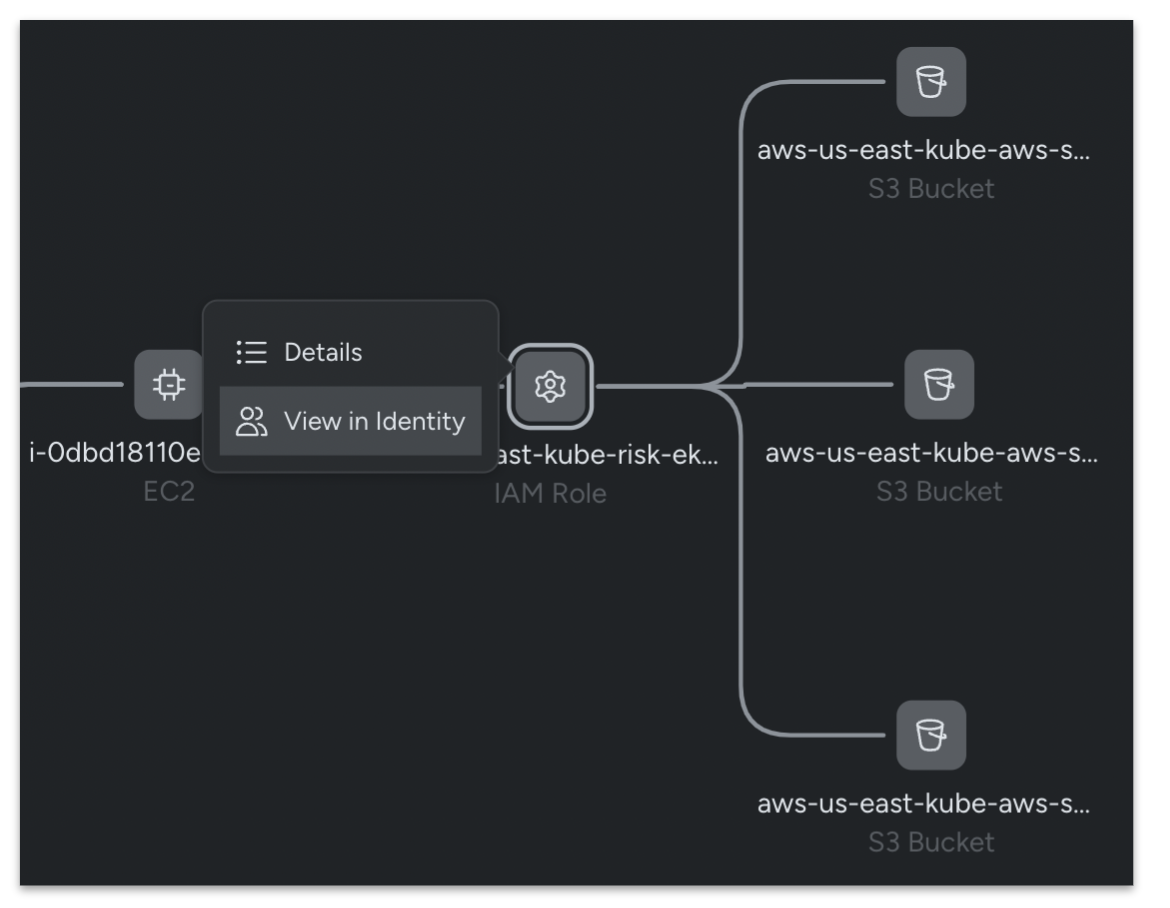
This visibility also helps teams to rapidly rightsize excessive permissions, such as by configuring them to permissions from before they were compromised by a malicious adversary.
Investigation workflow optimization
A single purpose-built platform can break silos and streamline downstream activities. Security becomes a critical and valuable business partner by delivering relevant, high-context guidance across key stakeholders. Rapid investigation findings enable prescriptive guidance for response actions across incident response, platform, developer, and DevSec teams. These accelerated findings allow response teams to initiate a response within five minutes, adhering to the five minute response standard outlined in the 5/5/5 Benchmark.
Closing the loop, the enhanced incident debrief findings these investigations provide (such as what misconfigurations, permissions, and vulnerabilities were abused to perpetuate the attack) can then be shared to tune and harden preventive controls. This focus on perpetual improvement to preventative controls helps ensure incidents are non-recurring, reducing organizational cloud risk.
Outpace cloud attacks with Sysdig’s enhanced investigations
The acceleration of cloud detection and response is critical to combat modern attacks. The automation-fueled pace of cloud attacks means that investigations must move even faster. Sydig’s enhanced investigations unlock security teams by increasing efficiency, reducing skill gaps, and empowering security and platform teams to make better-informed decisions, faster.
Join our upcoming webinar, Cloud Investigations in Just 5 Minutes, for a discussion with security experts on the evolution of cloud detection and response and its impacts.