Protecting Cloud Resources Like Never Before
The desire to quickly deploy and maintain third-party tools often leads organizations to grant broad, sometimes excessive permissions in their cloud environments. While this is convenient for onboarding and operations, it creates significant security vulnerabilities. Over-permissioned third-party accounts can access resources unnecessarily, increasing the risk of data exposure or unauthorized access if a third party is compromised. In fact, according to Wiz, “Over 90% of cloud security teams were not aware they gave high permissions to third-party vendors,” underscoring how easily these excessive permissions can slip under the radar.
As public cloud adoption grows, so does the integration of third-party vendors with customers’ AWS accounts–often to monitor infrastructure or collect logs. This access is typically granted through IAM roles that trust the vendor’s verified AWS account. However, this practice introduces cloud supply chain risks: If a vendor’s AWS account is compromised, an attacker could gain access to the same data as the vendor. According to Datadog, “an organization on average deploys 10.2 third-party integration roles (median 3), linked to 2.4 distinct vendors (median 2).”
“Overcoming the third-party business vs. security dilemma is challenging, since while the supply chain is an inherent risk, it is also essential to a business’s success. Shutting down third-party operations is equivalent to shutting down business operations.”
Sonrai Security understands that this “default trust” approach simply won’t work for effective cloud security. Third-party access often introduces unnecessary risks, including vendors retaining access after their contracts have ended, vendors having permissions to accounts or organizational units they don’t need, and over-permissioned roles created for convenience during setup.
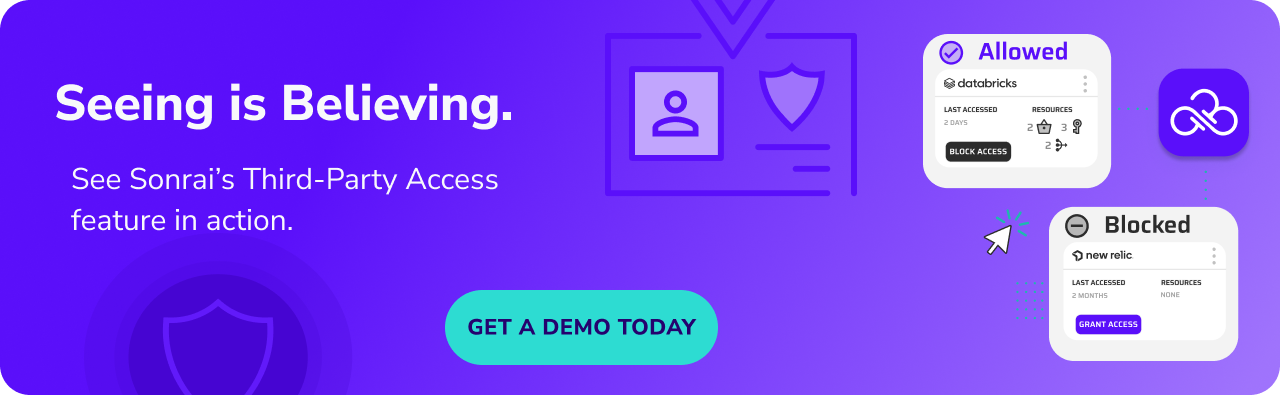
With Sonrai’s Third-Party Access feature and AWS’s new Resource Control Policies (RCPs), customers are empowered to make informed decisions about which third parties can access specific levels within their cloud environments, such as accounts or broader environments. This approach is straightforward and efficient but provides an extra layer of control over third-party access, reducing security risks while allowing organizations to manage cloud permissions on their terms.
A Breakthrough in Third-Party Access Control
Sonrai’s Third-Party Access feature leverages AWS’s Resource Control Policies (RCPs) to bring a new level of control to cloud environments. Unlike traditional IAM policies, which are assigned to identities, RCPs apply broad, organization-wide restrictions across entire AWS services or accounts within an organization. This setup allows organizations to restrict or permit external access to common services, such as Amazon S3 or AWS Secrets Manager, establishing a secure data perimeter for third-party access.
AWS describes RCPs as “a new type of organization policy that helps you centrally establish a data perimeter across your AWS environment.” By using RCPs, Sonrai’s Third-Party Access feature enables CloudOps teams to enforce access boundaries around critical cloud services, ensuring that external access to sensitive areas is tightly managed.
“The principle of least privilege is the modern security practice that can answer identity-management complexity – including that of third parties – in the cloud.”
In addition to controlling access for existing third-party relationships, Sonrai supports the least-privilege principle with an optional “default deny” state, blocking all third-party access until explicitly granted. This approach minimizes accidental exposure and gives CloudOps teams complete control over third-party permissions, helping organizations manage cloud security proactively.
Introducing Sonrai’s New Third-Party Access Feature
Sonrai’s Third-Party Access feature provides a powerful, easy-to-manage solution for controlling third-party permissions in real time. With AWS Resource Control Policies (RCPs) integrated directly into Sonrai’s Cloud Permissions Firewall, CloudOps teams gain precise control over who can access specific cloud resources and to what extent.
“Implement security controls to ensure secure access and adherence to the principle of least privilege when granting access to third-party SaaS providers.”
Here’s how it works:
Onboarding Phase: Establishing Secure Third-Party Access
- Evaluate Third-Party Access: Sonrai first evaluates all third-party access in the customer’s cloud environment, identifying who these third parties are and delineating what specific resources and accounts they currently access. Information includes what they have access to and if they have admin-level access and/or access to sensitive permissions.
- Create a Custom Access Policy: Based on this assessment and the customer’s choice to block or allow access, Sonrai automates the creation of a custom policy using AWS Resource Control Policies (RCPs) to block or allow access.
- Deploy the Policy: The customer, who owns the Cloud Permissions Firewall, deploys this newly written policy through AWS CloudFormation, setting up centralized, secure access controls across the cloud environment.
Updating Access: Managing Third-Party Access Requests in Real-Time
When a third-party requires changes to their access permissions, Sonrai’s Cloud Permissions Firewall enables a controlled process that minimizes risk and maintains security:
- Notification: When a third-party tries to access an account or resource that is blocked, a notification is sent to the Cloud Permissions Firewall owner.
- Approve/Deny: The Cloud Permissions Firewall owner decides if they want to approve or deny access.
- Deploy: Finally, to grant access, the Cloud Permissions Firewall owner updates the status in the UI and a new policy is deployed in a few clicks.
Optional Default-Deny State
Sonrai’s Cloud Permissions Firewall also offers a “default deny” setting, enabling customers to begin with a zero-access baseline for all third parties. This setting blocks access by default, allowing CloudOps teams to grant permissions only as needed, significantly reducing the risk of unauthorized access.
Limitations of Traditional Tools vs. Sonrai’s Third-Party Access
While traditional tools such as CIEM (Cloud Infrastructure Entitlement Management) and CSPM (Cloud Security Posture Management) offer visibility into cloud permissions, they often fall short in providing enforceable controls for third-party access. These tools may help teams identify third-party integrations but lack the centralized control needed to restrict permissions effectively across accounts or cloud services.
According to the Cloud Security Alliance, “Organizations tend to treat third parties as trusted entities. As such, third parties are granted access and control over sensitive resources.” Obviously, this approach just doesn’t work. Even trusted vendors should have guardrails around what they can access in your cloud, in case they are compromised themselves.
How Sonrai’s Solution Goes Further:
- Control Access Across Accounts or Services: Unlike traditional tools that focus on visibility alone, Sonrai’s Third-Party Access leverages AWS Resource Control Policies (RCPs) to set enforceable boundaries at the account or service level, restricting access for individual third parties broadly rather than focusing on individual resources.
- Automated Notification and Policy Updates: Rather than relying on reactive, manual oversight, Sonrai’s solution automatically notifies CloudOps teams of access requests in real time so they can make informed decisions. CloudOps teams can quickly take action with automated generation of updated policies through a streamlined process in the UI.
- Reduced Manual Effort: By integrating RCPs and automating access control workflows, Sonrai’s Third-Party Access reduces the manual work required to manage and enforce policies. Sonrai’s proactive permissions model ensures access decisions are centrally managed and logged, supporting efficient, secure management across the organization.
With Sonrai’s Third-Party Access feature, organizations gain a robust, modern solution that supports their cloud security objectives by providing centralized control, automated workflows, and comprehensive audit tracking—capabilities that traditional tools were never designed to achieve.
Real-World Benefits of Sonrai’s Third-Party Access Control
Sonrai’s Third-Party Access feature empowers organizations to manage third-party access securely and efficiently, providing substantial benefits across security, compliance, and operational efficiency:
- Preventing Data Exposure and Security Risks: With broad access policies in place, organizations can reduce the risk of unauthorized data access by limiting third-party permissions to specific accounts. This high-level control helps prevent accidental exposure of sensitive data, securing critical cloud environments from unintended third-party access.
- Simplified Compliance and Comprehensive Audit Trails: Compliance with data protection regulations and internal policies is easier with Sonrai’s built-in tracking and auditing capabilities. Every access request and permission change is logged, providing a clear audit trail that ensures accountability and enhances governance over third-party integrations.
- Operational Efficiency for CloudOps Teams: Sonrai’s Third-Party Access feature streamlines permissions management by automating notifications and centralizing access decisions within a single UI. This reduces the manual work required to manage policies and simplifies workflows, enabling CloudOps teams to maintain a secure environment without introducing operational delays.
By enabling centralized control, streamlined management, and comprehensive auditing, Sonrai’s Third-Party Access feature transforms how organizations secure and govern third-party access in their cloud environments. This proactive approach addresses common challenges with traditional tools, providing security and compliance with efficiency and ease.
Don’t Don’t Leave Third-Party Access to Chance
Cloud technology opens doors for growth, but it also introduces risks—especially when it comes to third-party access. Sonrai’s Third-Party Access feature offers a better approach, putting your team in control of permissions across your entire cloud environment.
With AWS RCPs, Sonrai’s solution allows you to set secure boundaries at the account or OU, ensuring third-party access is limited to only what’s essential. Whenever a third party requests access, Sonrai provides real-time alerts and a streamlined approval process that lets you make quick, informed decisions directly in the UI. Every action is logged, creating a detailed audit trail to support compliance and give you confidence in your cloud’s security posture.
With third-party integrations becoming both integral and risky, Sonrai’s Third-Party Access feature equips you to stay secure, proactive, and fully in control, allowing you to manage access effectively across your entire cloud environment.

